Policy Statement
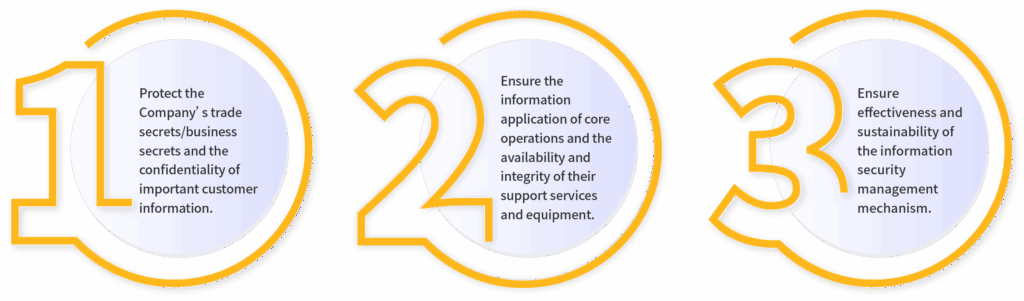
To ensure sustainable business development and fulfill our commitments to customers, MPI has established a comprehensive Information Security Policy, together with operational procedures and related guidelines. These measures aim to strengthen the information risk management framework, enhance information security mechanisms, and ensure the effective implementation of protective measures. By doing so, MPI raises overall information security standards and provides clear guidance for all employees and key business partners to follow.
Information Security Management Mechanism
MPI has implemented an ISO/IEC 27001-compliant Information Security Management System (ISMS), initially certified in 2015. On November 16, 2024, the Company successfully completed its transition certification to ISO/IEC 27001:2022, demonstrating continuous improvement and alignment with global best practices. The ISMS framework includes processes for information asset classification, risk assessment, and risk identification to ensure the effectiveness and continuity of information management. For core operational information systems, including equipment and network infrastructure, MPI conducts regular internal drills and employee training programs. These initiatives enhance information security awareness and strengthen the protection of trade secrets and customer confidentiality.
Information Security Organization and Responsibilities
 MPI has established a dedicated Information Security Organization responsible for preventive measures and incident response related to information security. The organization works to prevent trade secret leaks, protect IT systems, and ensure rapid response capabilities in the event of emergencies to restore normal operations swiftly and minimize potential damages.
MPI has established a dedicated Information Security Organization responsible for preventive measures and incident response related to information security. The organization works to prevent trade secret leaks, protect IT systems, and ensure rapid response capabilities in the event of emergencies to restore normal operations swiftly and minimize potential damages.
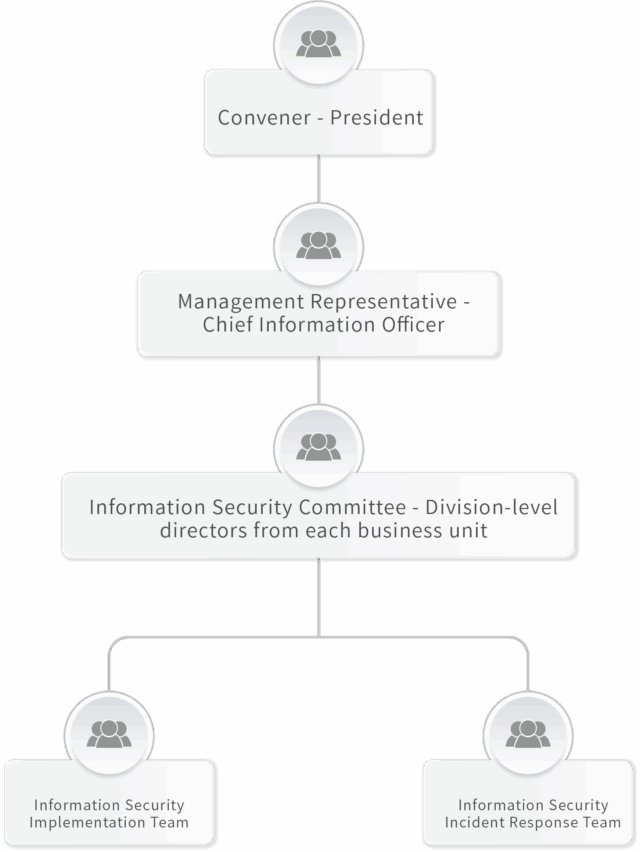
The Information Security Organization consists of the President, the Information Security Committee, the Management Representative, the Information Security Incident Response Team, the Information Security Implementation Team, and unit representatives from across the Company. The structure includes three dedicated information security personnel, and MPI also consults external experts, industry professionals, and academic institutions to strengthen collaboration, share knowledge, and develop practical measures for mitigating potential information security threats.
In 2024, MPI’s dedicated information security personnel held 24 regular information security meetings, reporting biweekly to the Management Representative to ensure ongoing oversight. Additionally, one Information Security Management Review Meeting was conducted to evaluate the effectiveness of security measures. On January 14, 2025, MPI convened a Board-level Information Security Performance Meeting to present the 2024 implementation results, ensuring that the Company’s overall information security and protection of trade secrets are comprehensively supervised and effectively managed.
| Organization Name | Roles and Responsibilities |
|---|---|
| Convenor | The President serves as the convener, responsible for approving, endorsing, and overseeing information security policies, allocating and coordinating security responsibilities, and monitoring the overall effectiveness of information security operations. |
| Management Representative | The Chief Information Officer (CIO) serves as the management representative, responsible for overseeing the operation of the Information Security Management System (ISMS), ensuring compliance with stakeholder and regulatory security requirements, and establishing secure and reliable information processes to safeguard the Company’s business continuity. |
| Information Security Committee | The division-level directors from each business unit serve as committee members, responsible for coordinating cross-departmental information security responsibilities and aligning annual security goals and plans across the organization. |
| Information Security Incident Response Team | Responsible for managing information security incident responses and coordinating with relevant units. Duties include implementing security-related policies, plans, and measures, as well as conducting technical assessments, research, and infrastructure implementation. |
| Information Security Implementation Team | Responsible for the continuous improvement of the information security system. Oversees overall planning and collaborates closely with departmental representatives to ensure the effective execution of all information security operations. |
| Departmental Information Security Representatives | Appointed by each department as seed personnel to support and execute the daily operations of the information security system according to their assigned responsibilities. |